Penetration Testing vs. Red Teaming: Key Differences and When to Use Each
Penetration testing and red teaming are the offensive measures to test your security; they have different endpoints as objectives.
A penetration test is a simulated cyber-attack activity against a system to check for the presence of exploitable vulnerabilities. It is a disciplined practice that “uncovers vulnerabilities in your systems with all the simulated attack”.
A Penetration test leverages automated scans and manual exploits to identify misconfigurations, unpatched software, weak passwords, and other flaws. In contrast, red teaming simulates a real-world adversary.
A red team “functions like a real cyber threat, combining hacking methodology and social engineering with stealth tactics to test the digital defenses of your business”. Red teaming takes a comprehensive approach, attempting to achieve specific objectives/goals of the activity by any means necessary, often without the defenders knowing it is a test.
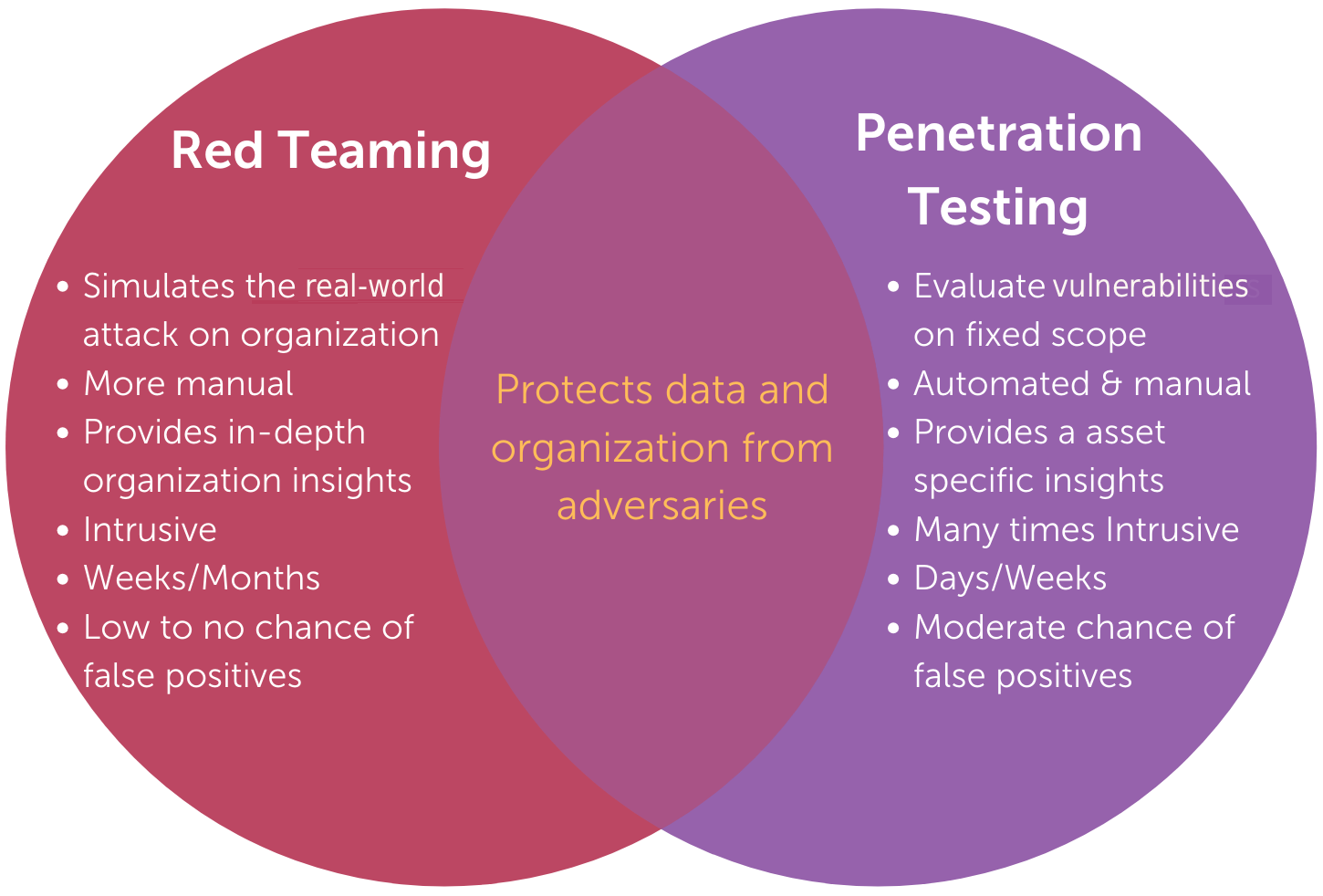
The key differences between both include:
Objective
Penetration testing originated as the assessment of defects within a predefined scope, such as an application or a network. While modern penetration tests can include chained or multi-step attacks, the key distinction is that testers focus on uncovering and demonstrating vulnerabilities, whereas red teams pursue broader objectives (e.g., data theft or persistence) using those vulnerabilities as a means to an end. Red teaming, however, is brought about by assessing how the organization can detect and respond to conditions from an actual attack.
Scope
A penetration test is usually limited to specified systems or applications (such as a web app or cloud infrastructure). A red team can cover a broader attack surface, including networks, applications, social engineering, and in some cases physical security. However, physical intrusions are only attempted if they are explicitly included in the rules of engagement, since many organizations exclude them for safety and liability reasons.
Approach
Penetration testing is a controlled, systematic attack using known techniques to expose weaknesses. Red teaming is a threat-led, adversarial simulation. Red teams often work covertly, avoiding detection to mimic an Advanced Persistent Threat (APT).
Techniques
Vulnerability scans, exploitation tools, and configuration testing are the main tools used by testers during a penetration test. Red teams have a much broader arsenal than that of network hacking, phishing emails, social engineering (through phone calls or even physical intrusion), custom built malware, and various other advanced tactics, to meet their aims.
Outcome/Focus
The extent of success in penetration testing can be measured by the number of vulnerabilities that have been uncovered and remediated, whereas red teaming would test success by whether the intended objective (like data ex-filtration) was met without detection.
Pentesting vs Red Teaming: Differences
| Factor | Penetration Testing | Red Team |
|---|---|---|
| Objective | Identify and fix vulnerabilities | Test detection and security resilience to real attacks |
| Scope | Defined targets (web apps, networks, etc.) | Broad attack surface (people, tech, processes, physical) |
| Approach | Controlled, systematic simulated attacks | Threat-led, adversarial simulation with stealth |
| Techniques | Vulnerability scanning, exploitation, config testing | Ethical hacking, phishing, social engineering, physical breach |
| Best for | Compliance checks, vulnerability assessments | Testing detection/response, real-world security posture |
Although both penetration testing and red teaming involve skilled security experts, they differ in scope, objectives, and execution.
Penetration Testing — Use Cases
Organizations conduct penetration testing to quickly identify and remedy vulnerabilities. For example, PCI DSS explicitly requires periodic penetration testing (annually and after major changes). Other regulations like SOX and HIPAA do not mandate penetration testing directly, but they require security and risk assessments, and many organizations use penetration testing as a recognized best practice to help meet those obligations. Penetration testing is also valuable when new applications are brought into production, following major upgrades of applications, or when any system requires a security review.
It’s a good first step for companies to evaluate their technical defenses. Small to medium businesses or teams with limited security maturity often start with penetration testing to ensure that obvious flaws are addressed.
Red Teaming — Primary Purpose
Red teaming engagements are used when an organization has a more mature security program and wants to test its overall readiness. If a company already runs regular penetration tests and has patched the most known vulnerabilities, a red team exercise can simulate an attack on an organization's security posture.
Red teaming evaluates an organization’s people, processes, and technology under pressure. It is ideal for testing Security Operations (SOC) and Incident Response (IR) teams.
The purpose is to answer questions like: Can our security team detect this attack? How quickly can they respond? Red teaming by design is meant to validate detection and response.
In practice, sectors like finance, government, or large enterprises—where APTs or targeted threats are a concern—commonly hire red teaming services to simulate advanced threats. A red teaming engagement “Red teaming is not suitable for all organizations,” but should be used by organizations “with mature security programs” that want to thoroughly test their defenses.

Tools and Methodologies
Automated scanners along with well-known frameworks like Nessus, Nmap, Burp and Metasploit form the basis of penetration testing for methodical identification and exploitation of target vulnerabilities.
Real-world attacker trade craft gets replicated by red teams through the integration of OSINT platforms and phishing kits with custom malware and covert C2 frameworks such as Cobalt Strike and Empire to operate across technical, social and occasionally physical attack vectors.
Penetration Testing: Tool-Centric, Methodical
Like other cyber specialists, Penetration testers move within set limits and deadlines, making use of standard playbooks like PTES and OWASP Top 10.
The initial part of the process will be recon with Nmap scans, banner grabs, and a few credential-brute-force scripts. Then automated scans will follow, using Nessus, OpenVAS or Burp Suite, and OWASP ZAP.
Exploitation mainly follows a framework, using Metasploit modules and published CVE proofs of concept. This is followed by a tight feedback loop of validation and report writing. The goal: enumerate every in-scope weakness, prove exploitability, and hand the client a prioritized remediation list.
Red Teaming: Adversary Emulation, Threat Intelligence-Led
Red teams simulate live threat actors. They front-load engagements with deep OSINT collection, map their campaign to MITRE ATT&CK, and craft bespoke attack paths.
The toolkit is wider: practically a complete suite of pen test tools, advanced command & control frameworks, phishing tool-kits, custom droppers, and physical access tools (RFID cloners, hardware implants, lock picks) if the rules of engagement allow.
The operation runs in parallel streams (initial foothold, privilege escalation, and lateral movement) while maintaining covert C2 channels to keep the payloads covert. Success is measured by how convincingly the team can think like, and remain hidden like a real intruder, not by raw vulnerability counts.
Team Structure and Mindset
The makeup of a penetration testing team is usually different from a red team.
Team Composition
A penetration testing team is usually a tight knot of deep expertise in network, web, and host, who swoop in for a focused technical assessment.
Red teams, by contrast, contain more experienced members like exploit developers, social-engineering pros, physical-security folks, and intel analysts, all working under one roof, so they assess the organization from every angle.
Blue-Team Awareness
As the penetration test is a scheduled drill, the defenders often know it’s coming and may even tail the testers in real time, treating the exercise as a controlled fire drill. When a red team rolls in, nobody turns on the sirens ahead of time—the blue team is left to spot the breach on their own, exposing blind spots in monitoring and incident response.
Tactical Mindset
The Penetration testers play “catch-’em-all,” and will document all the vulnerabilities that they find as time permits. Red teamers pick one mission—say, “steal the crown jewel without being noticed”—and pursue it with attacker realism, chaining exploits, pivoting laterally, and vanishing into the noise.
Duration & Resources
A typical pentest wraps in a week or two, driven by a small roster and a tight statement of work. Red-team engagements often last three to four weeks or longer, involving several sub-teams at the same time. These include network breaches, phishing operations, and physical intrusions. This setup provides the operation with both breadth and endurance.
Benefits and Limitations
Both methods help assess security, and both deliver but have some trade-offs.
1: Penetration Testing
Benefits
The most redeeming characteristic is a quick way to identify live vulnerabilities, allowing an organization to remediate weaknesses before an attacker takes advantage of them. Pentests are relatively scoped and often cost-effective; pentests are often favored to help meet compliance and certification standards (i.e., PCI DSS, ISO 27001, etc.). Pentests can also be used periodically (quarterly or annually) to compare against a baseline of security posture.
Limitations
Although pentests provide a good review of the tactics and techniques of an attacker, they do not provide insight into an organization’s ability to detect or respond to an attack. Because the defenders know a pentest is scheduled, the exercise is not stealthy and is sometimes noisy.
This means teams can be on high alert, and defenses may look stronger than they truly are. Pentests also cover only the systems in scope and may miss chained or advanced attacks that fall outside the determined parameter or scope.
For example, a penetration test might miss a multi-stage attack where attackers exploit an unpatched vulnerability in outdated or unsupported third-party software.
2: Red Teaming
Benefits
Provides a practical assessment of security, exposing not only technical vulnerabilities, but also weaknesses in processes and in people. Red teaming simulates advanced attackers so that organisations can enhance incident response and address gaps in their monitoring processes.
The exercise “evaluates the organization’s threat detection and response capabilities”. If successful, it confirms that security controls and team training are effective under pressure.
Limitations
Red team engagements require significant time, expertise, and expense. They are most valuable for organizations that have already addressed basic vulnerabilities. Red team assessments “should be performed by organizations with mature security programs” that have already done penetration testing and applied patches.
A poorly prepared organization may not benefit from red teaming because it could get overwhelmed by even simple attacks. In addition, red team exercises can cause disruption (especially if it is physical) and may have higher chances of danger (if it is not managed properly).
For example, a red team exercise can disrupt the organization’s operations, targeting physical security by causing alarms to go off at an inappropriate time.
When to Choose Each?
Whether you should choose penetration testing or red teaming largely depends on the matters of your goals and maturity. The relevant factors are your industry and business size, your level of current security maturity, your threat profile, and any compliance requirements you have. In general:
-
Choose Penetration Testing if… you want a comprehensive list of vulnerabilities in specific systems and need to meet regulatory requirements. If your security program is still developing, penetration tests are an effective way to quickly strengthen defenses. They are also appropriate when you have a limited budget or time for assessments.
-
Choose Red Teaming if… you have a mature security operation and want to evaluate your defenses end-to-end. If your organization is concerned about sophisticated threats (e.g. APT-style attacks) or needs to test its incident response and security monitoring, a red team engagement is appropriate. For example, enterprises and government agencies often use red teams to simulate targeted attacks and train their SOC teams.
Often, organizations benefit from both. A common strategy is to start with regular penetration tests to establish a strong security baseline, then progress to periodic red team exercises for advanced validation.
When in doubt, consider your immediate goals: “fix known issues” suggests penetration testing, whereas “stress-test defenses against real attack scenarios” suggests red teaming.
Overall, penetration testing and red teaming are complementary. Penetration testing gives you technical breadth (many vulnerabilities identified), while red teams give you operational depth (how well you withstand an actual attack). Both are valuable tools in a security arsenal.
